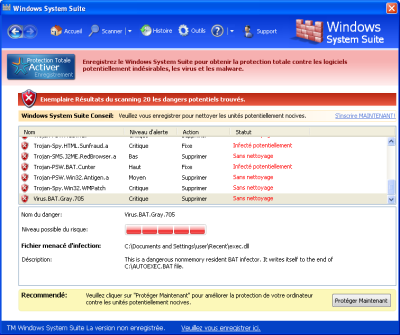
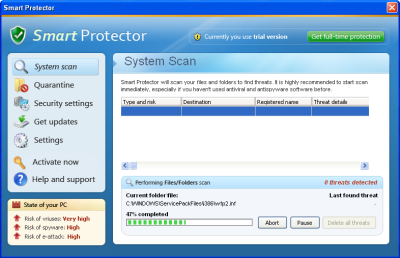
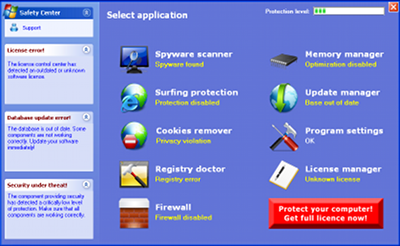
...and remains undetected.
Malware creators have to bypass antivirus protections to infect users. To be undetectable, the executable binary must not have a recognizable pattern.
Packing the file is one of the method used. It was a good trick to hide the code and reduce the size of the binary. But antivirus softwares can detect home made packers, entropy, and most of them can unpack known packers routines to scan the original file.
So, another protection was added
to cypher the packed file:

On the picture, the work done in memory:
The executable contains a
cyphered UPX binary that contains the
malware itself. The first stub uncypher the binary (green arrow).
Let's have a look at the code: in red, the uncypher routine doing the job.

Once done, the code appears in clear. Simple, but effective:
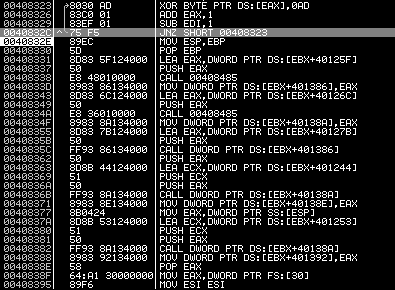
Then the UPX stub unpack the Malware code (blue arrow) and run it.
A well known malware file can be undetectable (until an antivirus detects the first shell).
To remain undetected, the uncypher routine must be often changed:
- Some "junk code" is inserted before and after it (jumps, calls, various real and unnecessary routines),
- Some various protections can slow the analyst work,
- Modification of the file every time it is downloaded. A few bytes are changed (one is enough) to generate a new hash.
Then, every day, a file that contain a well known infection, is released. The file looks new (different size, no recognizable patterns) and malware analysts have to work on it to detect what seems to be new but is NOT. Virus Total returns a poor detection (or 0 detection sometimes).